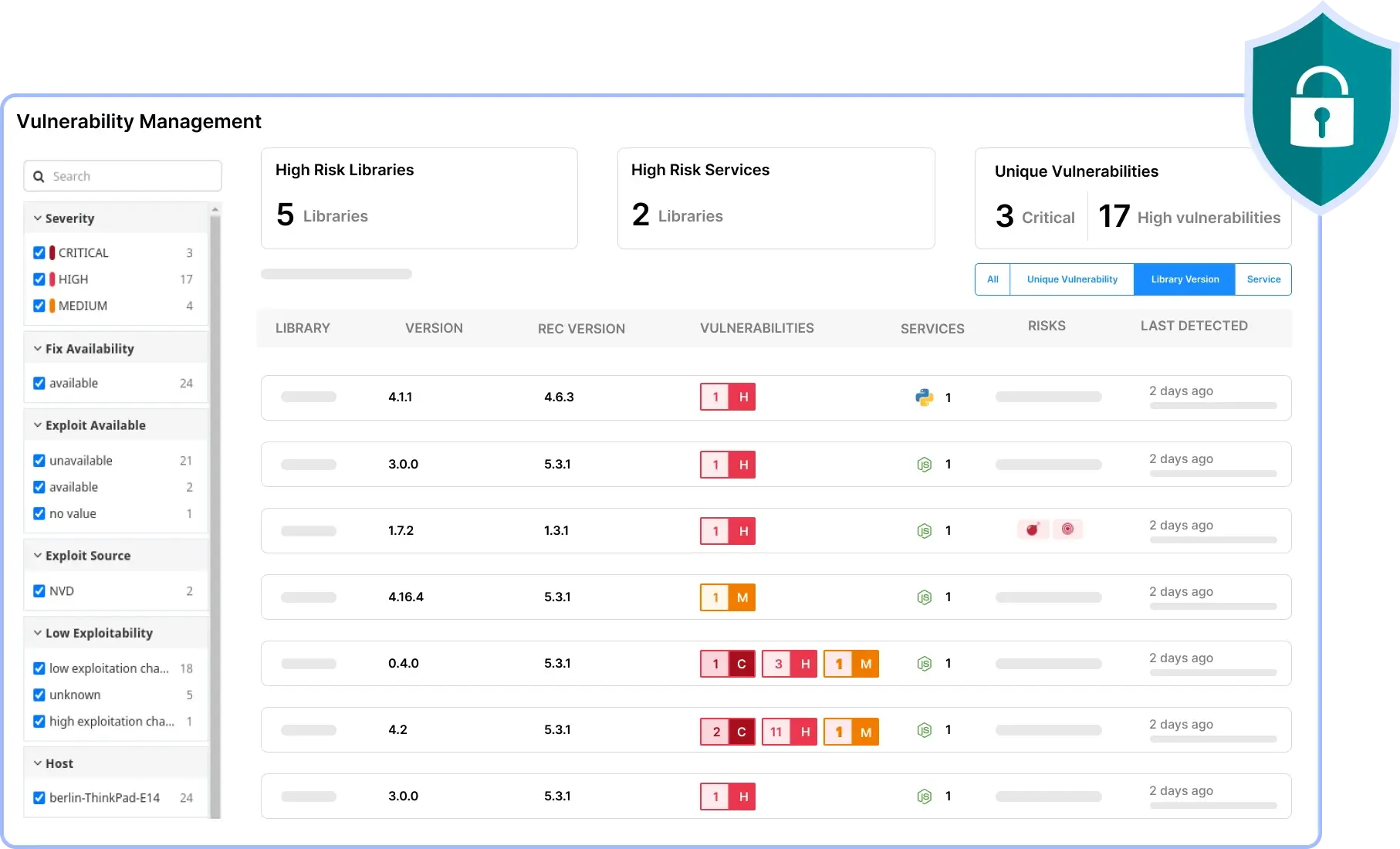
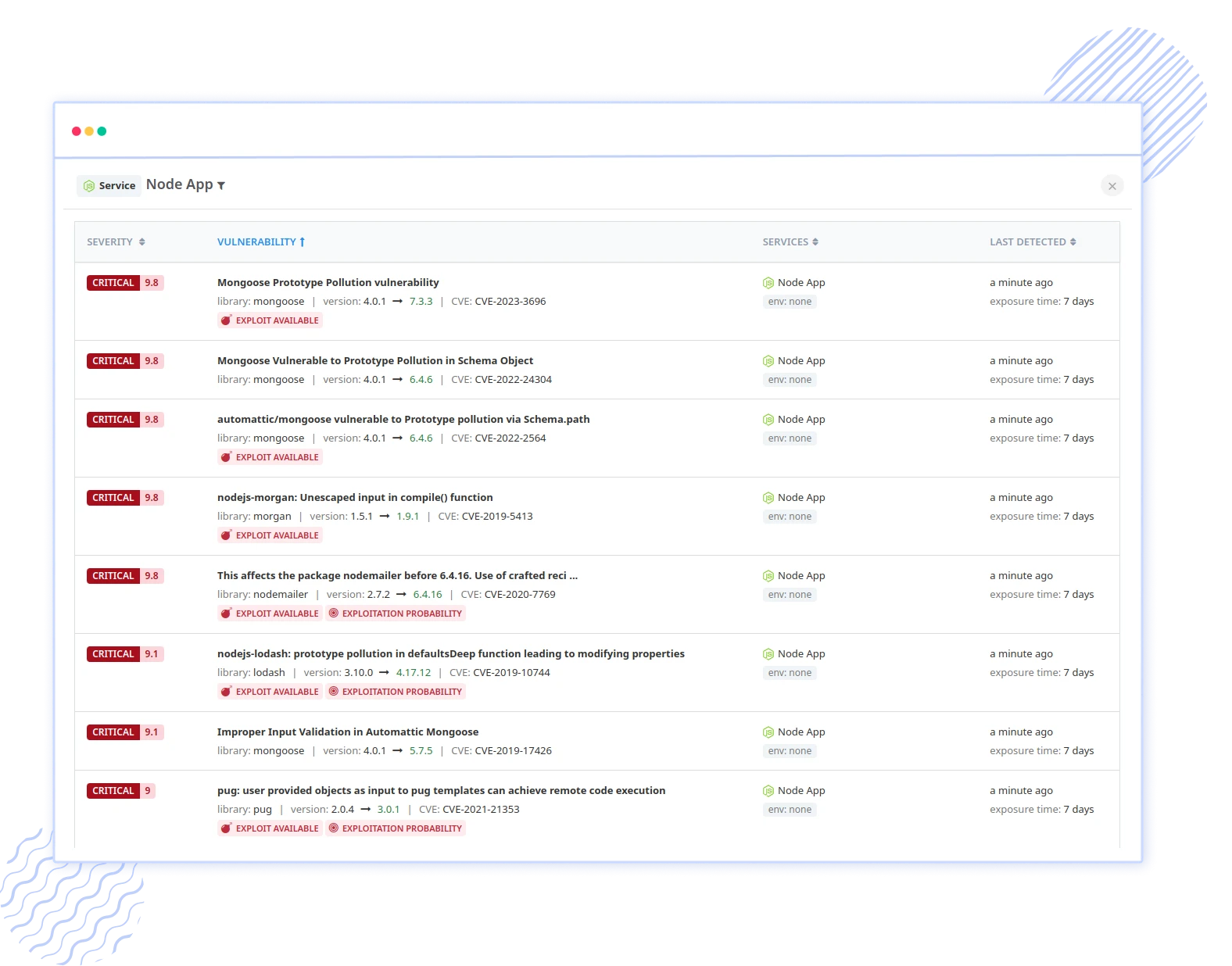
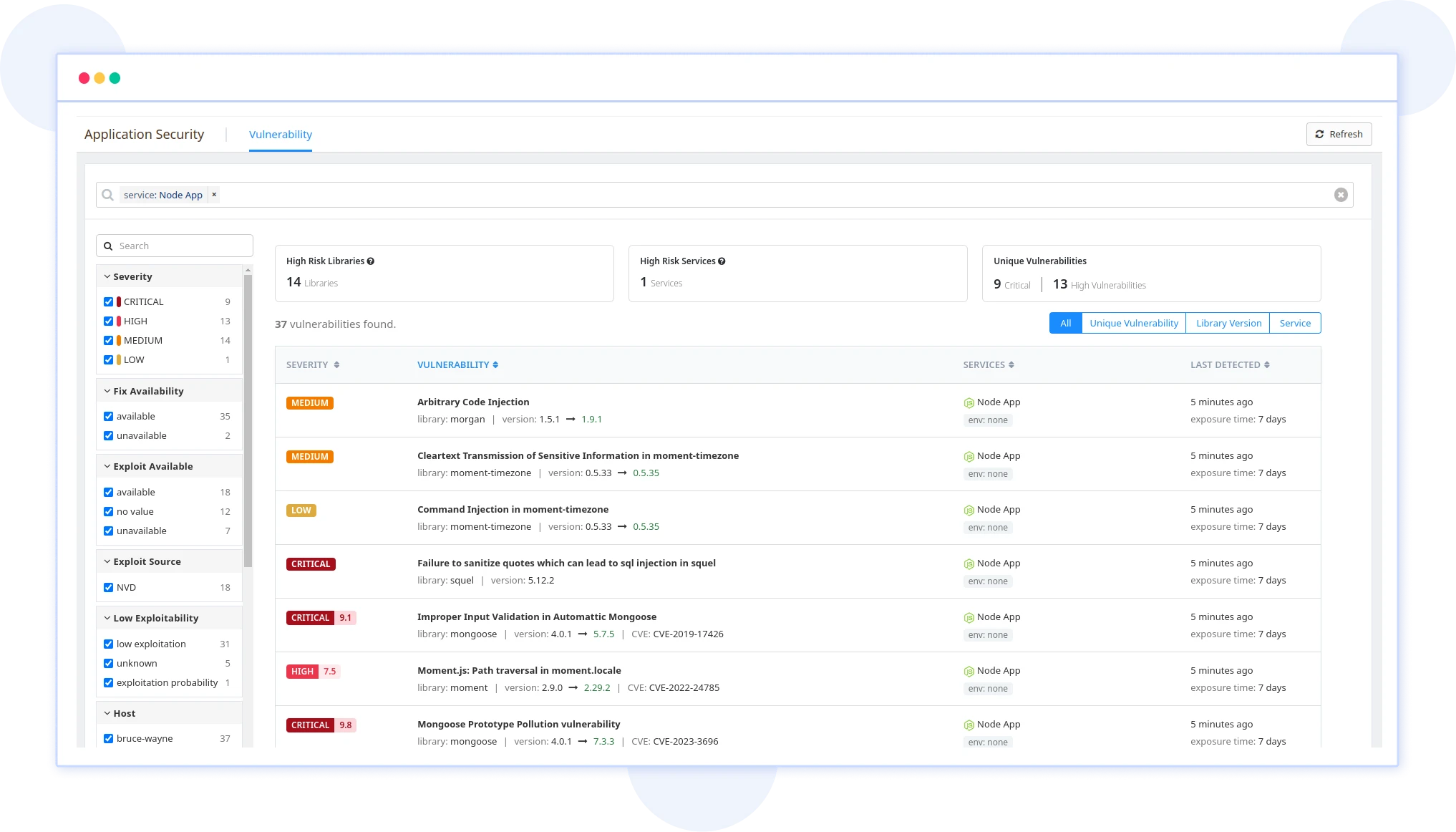
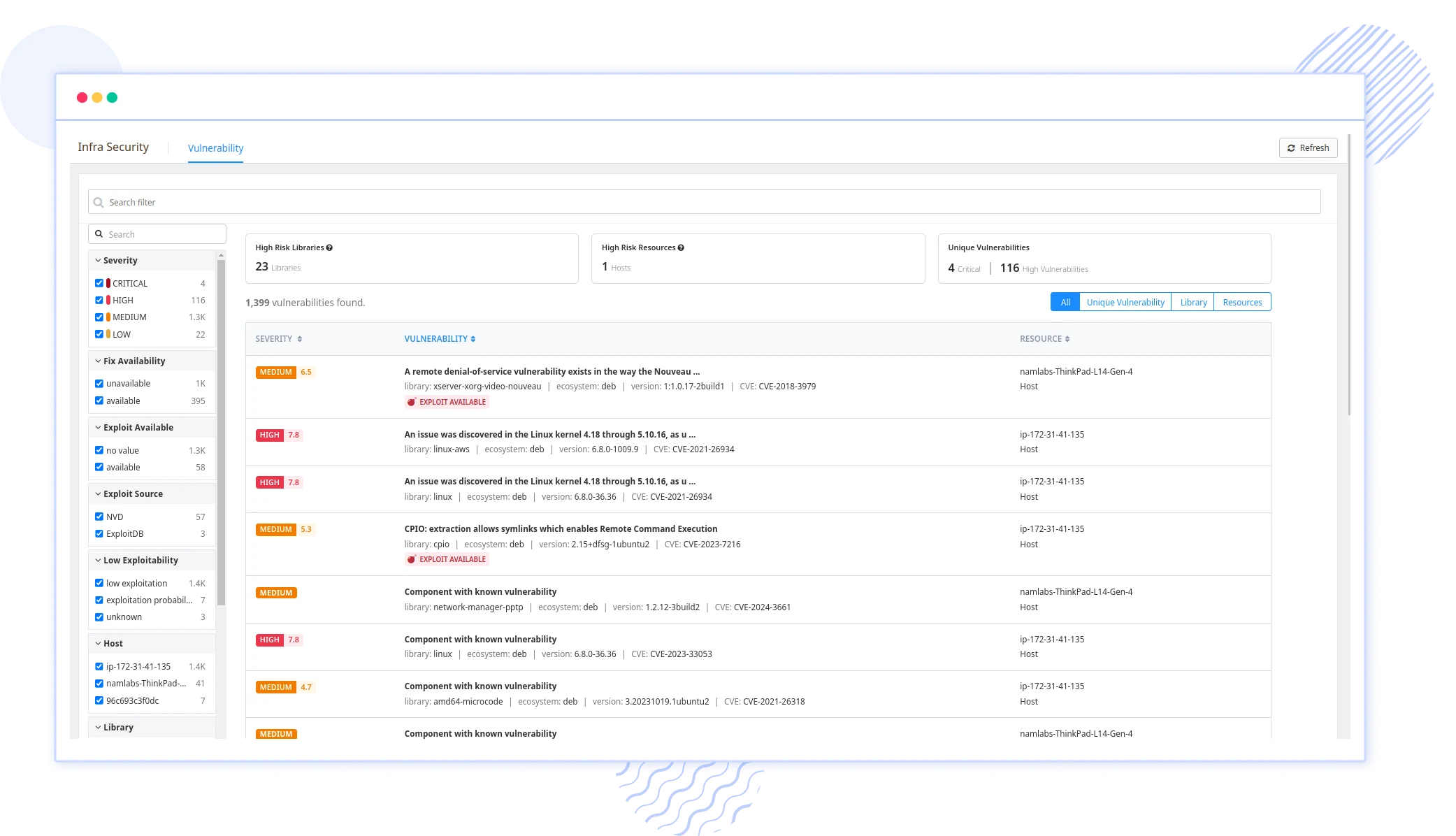
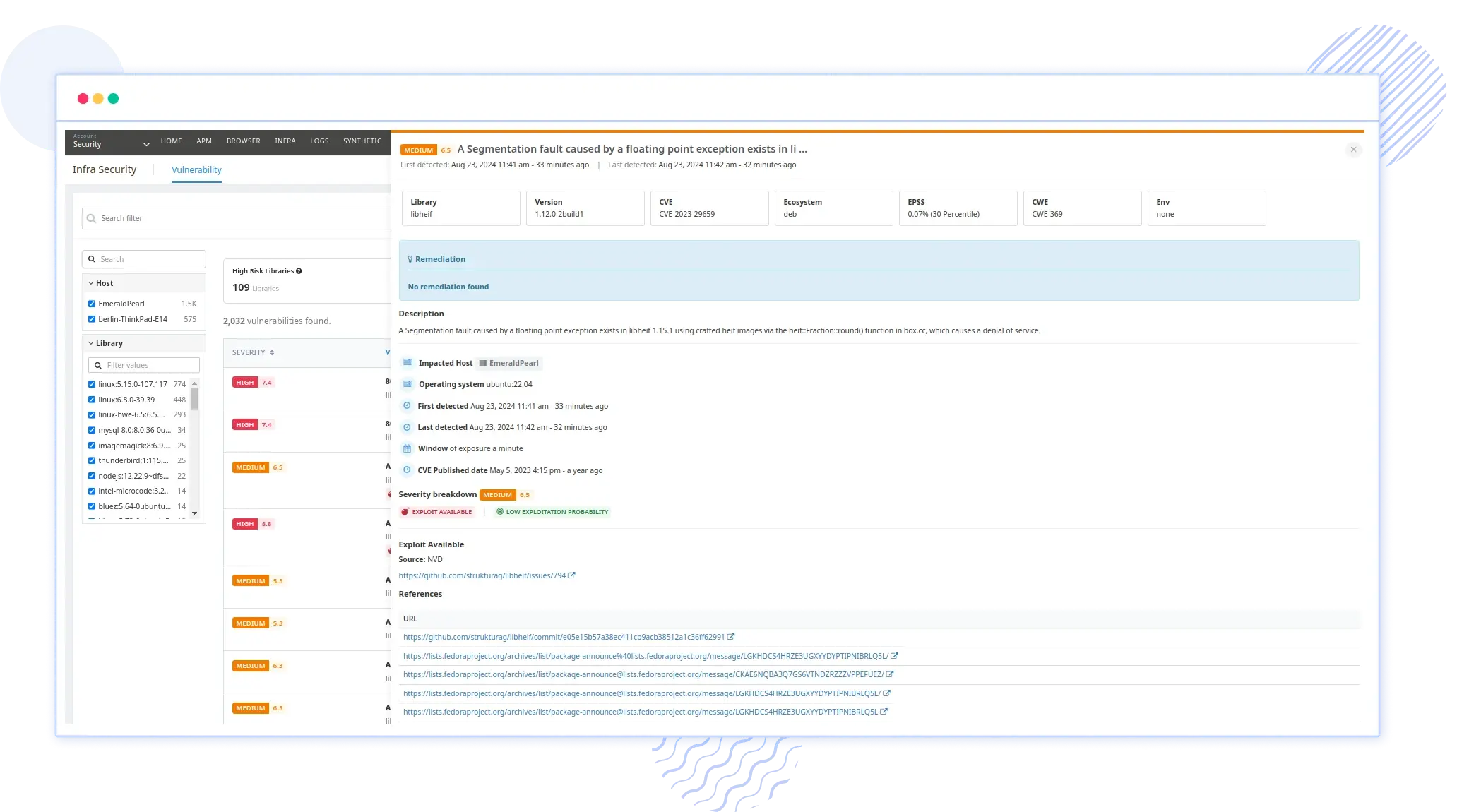
Vulnerability Management
Identify and prioritize security threats in real-time with our vulnerability management solution. Receive insights and custom alerts to tackle critical issues swiftly. Enhance your security posture and accelerate your response to potential risks, ensuring comprehensive protection for your systems.









 +1-760-465-2330
+1-760-465-2330


