Log Analysis Monitoring
Monitor your log data in real-time for unmatched visibility into application health with Atatus's log analyzer tool. Quickly resolve issues and tackle security threats effectively to ensure a secure and stable operational environment.
Sign Up for Free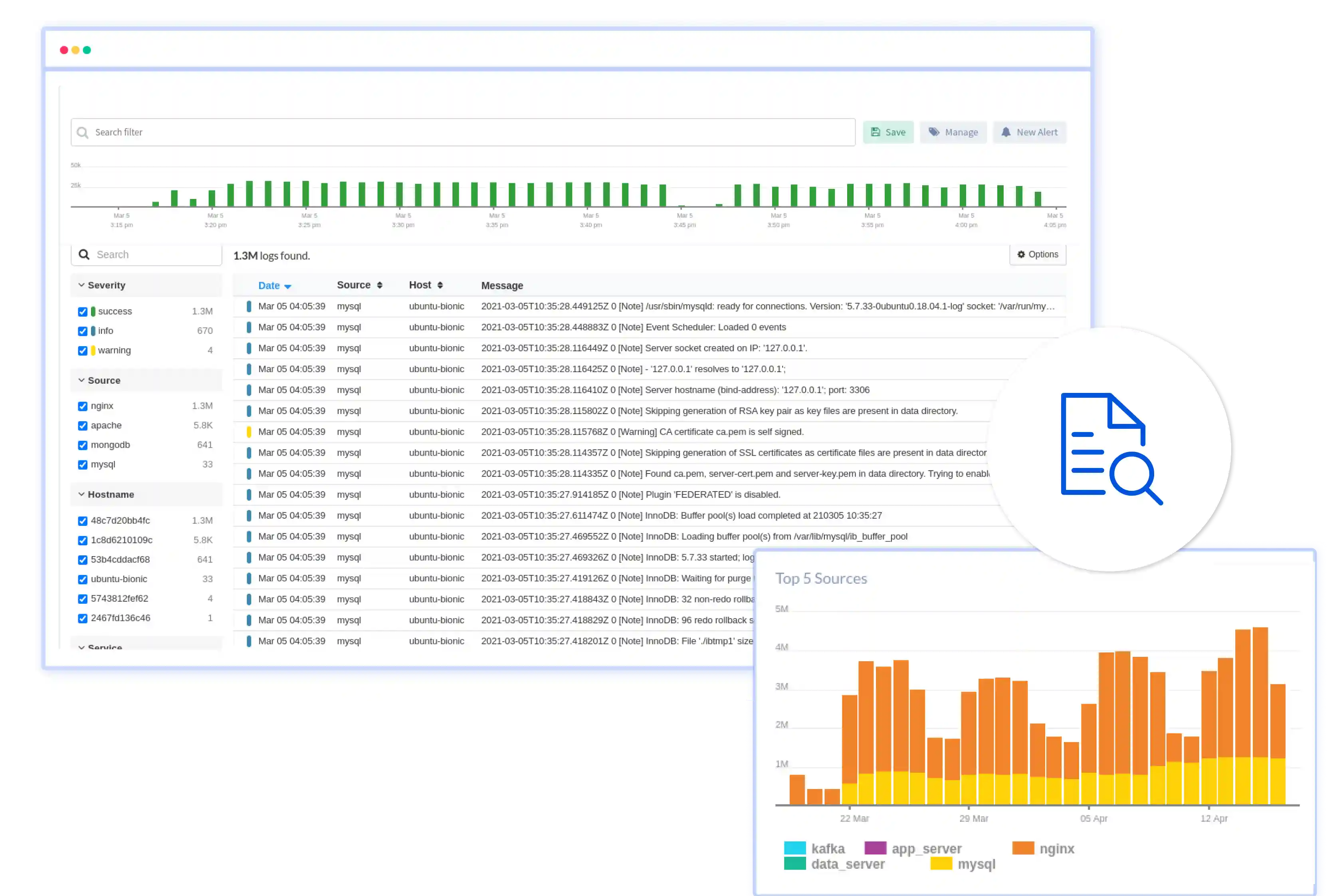




 +1-415-800-4104
+1-415-800-4104


